forked from Shiloh/githaven
Fork of #14483, but [gave up MasterKey](https://github.com/go-gitea/gitea/pull/14483#issuecomment-1350728557), and fixed some problems. Close #12065. Needed by #13539. Featrues: - Secrets for repo and org, not user yet. - Use SecretKey to encrypte/encrypt secrets. - Trim spaces of secret value. - Add a new locale ini block, to make it easy to support secrets for user. Snapshots: Repo level secrets: 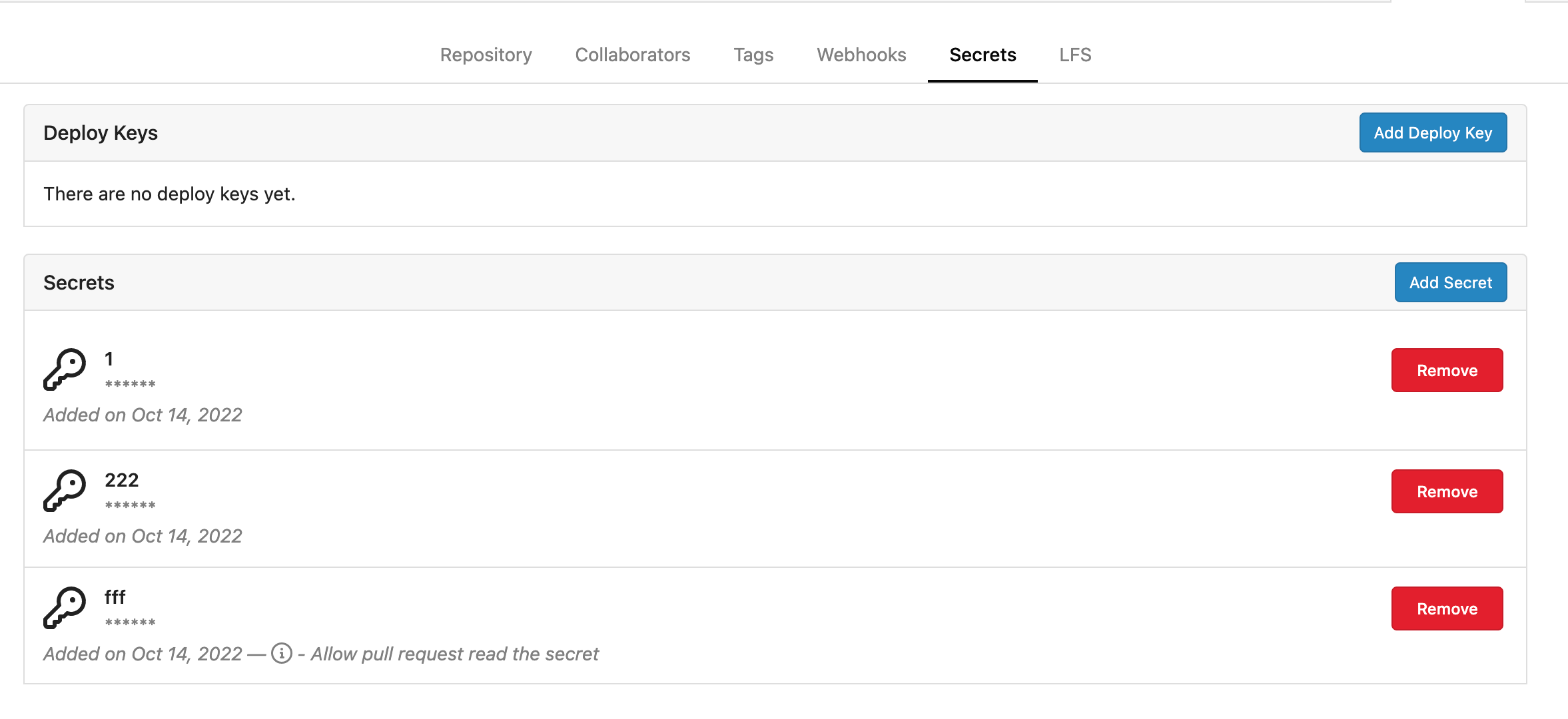 Rrg level secrets 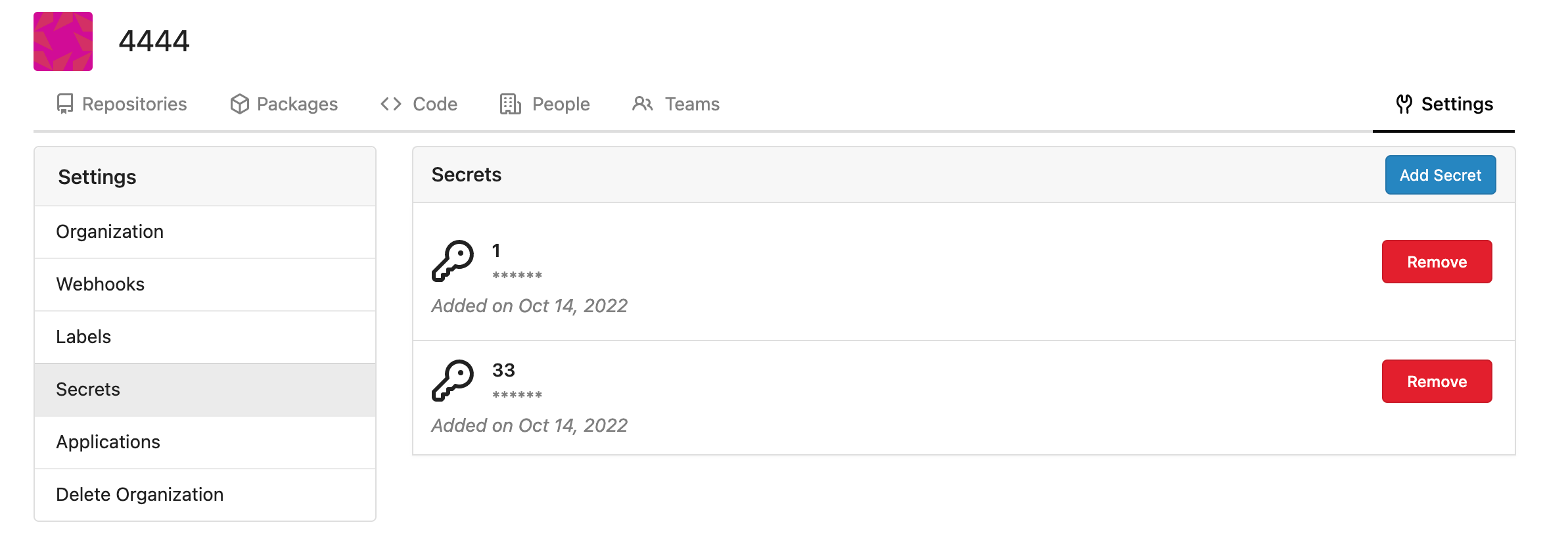 Co-authored-by: Lauris BH <lauris@nix.lv> Co-authored-by: Lunny Xiao <xiaolunwen@gmail.com> Co-authored-by: wxiaoguang <wxiaoguang@gmail.com> Co-authored-by: delvh <dev.lh@web.de> Co-authored-by: KN4CK3R <admin@oldschoolhack.me>
37 lines
1.2 KiB
Markdown
37 lines
1.2 KiB
Markdown
---
|
|
date: "2022-12-19T21:26:00+08:00"
|
|
title: "Encrypted secrets"
|
|
slug: "secrets/overview"
|
|
draft: false
|
|
toc: false
|
|
menu:
|
|
sidebar:
|
|
parent: "secrets"
|
|
name: "Overview"
|
|
weight: 1
|
|
identifier: "overview"
|
|
---
|
|
|
|
# Encrypted secrets
|
|
|
|
Encrypted secrets allow you to store sensitive information in your organization or repository.
|
|
Secrets are available on Gitea 1.19+.
|
|
|
|
# Naming your secrets
|
|
|
|
The following rules apply to secret names:
|
|
|
|
Secret names can only contain alphanumeric characters (`[a-z]`, `[A-Z]`, `[0-9]`) or underscores (`_`). Spaces are not allowed.
|
|
|
|
Secret names must not start with the `GITHUB_` and `GITEA_` prefix.
|
|
|
|
Secret names must not start with a number.
|
|
|
|
Secret names are not case-sensitive.
|
|
|
|
Secret names must be unique at the level they are created at.
|
|
|
|
For example, a secret created at the repository level must have a unique name in that repository, and a secret created at the organization level must have a unique name at that level.
|
|
|
|
If a secret with the same name exists at multiple levels, the secret at the lowest level takes precedence. For example, if an organization-level secret has the same name as a repository-level secret, then the repository-level secret takes precedence.
|